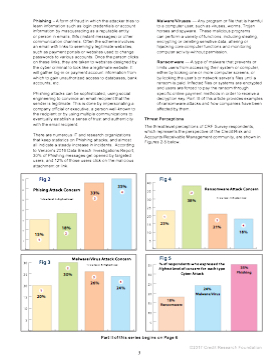
Phishing – A form of fraud in which the attacker tries to learn information such as login credentials or account information by masquerading as a reputable entity or person in emails, IMs (instant messages) or other communication channels. Often the scheme involves an email with links to seemingly legitimate websites, such as payment portals or websites used to change passwords to various accounts. Once the person clicks on these links, they are taken to websites designed by the cyber criminal to look like a legitimate website. It will gather log-in or payment account information from which to gain unauthorized access to databases, bank accounts, etc. Phishing attacks can be sophisticated, using social engineering to convince an email recipient that the sender is legitimate. This is done by impersonating a company of cial or executive, a person well-known to the recipient or by using multiple communications to eventually establish a sense of trust and authenticity with the email recipient. There are numerous IT and research organizations that keep statistics on Phishing attacks, and almost all indicate a steady increase in incidents. According to Verizon's 2016 Data Breach Investigations Report, 30% of Phishing messages get opened by targeted users, and 12% of those users click on the malicious attachment or link. Malware/Viruses — Any program or le that is harmful to a computer user, such as viruses, worms, Trojan horses and spyware. These malicious programs can perform a variety of functions, including stealing, encrypting or deleting sensitive data, altering or hijacking core computer functions and monitoring computer activity without permission. Ransomware — A type of malware that prevents or limits users from accessing their system or computer, either by locking one or more computer screens, or by locking the user’s or network server’s les until a ransom is paid. Infected les or systems are encrypted and users are forced to pay the ransom through speci c online payment methods in order to receive a decryption key. Part III of this article provides examples of ransomware attacks and how companies have been affected by them. Threat Perceptions The threat level perceptions of CRF Survey respondents, which represents the perspective of the Credit Risk and Accounts Receivable Management community, are shown in Figures 2-5 below. Fig 4 40 35 30 25 20 15 10 5 Ransomware Attack Concern 1=low level, 4=highest level 2 38% 1 23% 3 21% 4 18% 35 30 25 20 15 10 5 Fig 2 Phising Attack Concern 1=low level, 4=highest level 35% 4 15% 1 18% 2 33% 3 Fig 5 % of respondents who expressed the highest level of concern for each type Cyber Attack 5 35 30 25 20 15 10 18% Ransomware 24% Malware/Virus 35% Phishing 30 Fig 3 25 20 15 10 5 Malware/Virus Attack Concern 1=low level, 4=highest level 2 30% 3 26% 4 24% 1 20% Part II of this series begins on Page 6 3 ©2017 Credit Research Foundation